Findings of the detector that identify an anomaly in the same file and method as the known misuse.
| Hit |
Rank |
Confidence |
Confidence String |
Pattern Support |
Pattern Violation |
Target Environment Mapping |
|
?
|
1207 |
0.25170934 |
((pattern support = 12 / 791)(pattern violations = 1 / 60)(violation support = 1 / 10)(overlap = 1 - (1 / 8))) / 4 |
12 |
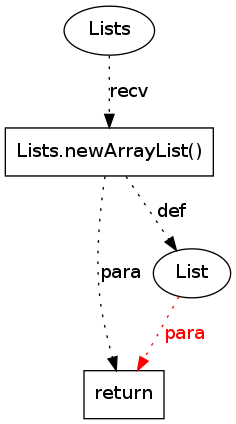
|
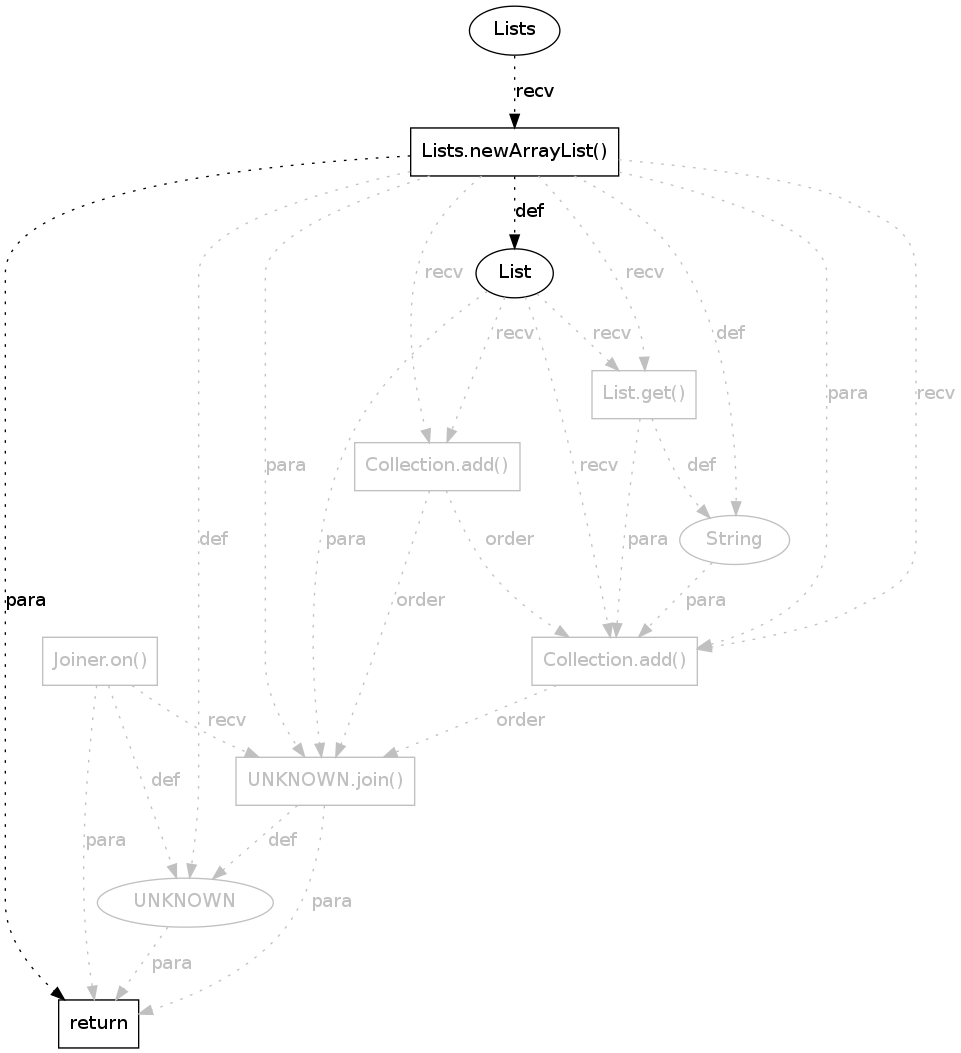
|
|
?
|
1274 |
0.24910212 |
((pattern support = 10 / 791)(pattern violations = 1 / 28)(violation support = 1 / 11)(overlap = 1 - (1 / 7))) / 4 |
10 |
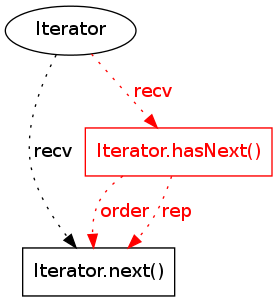
|
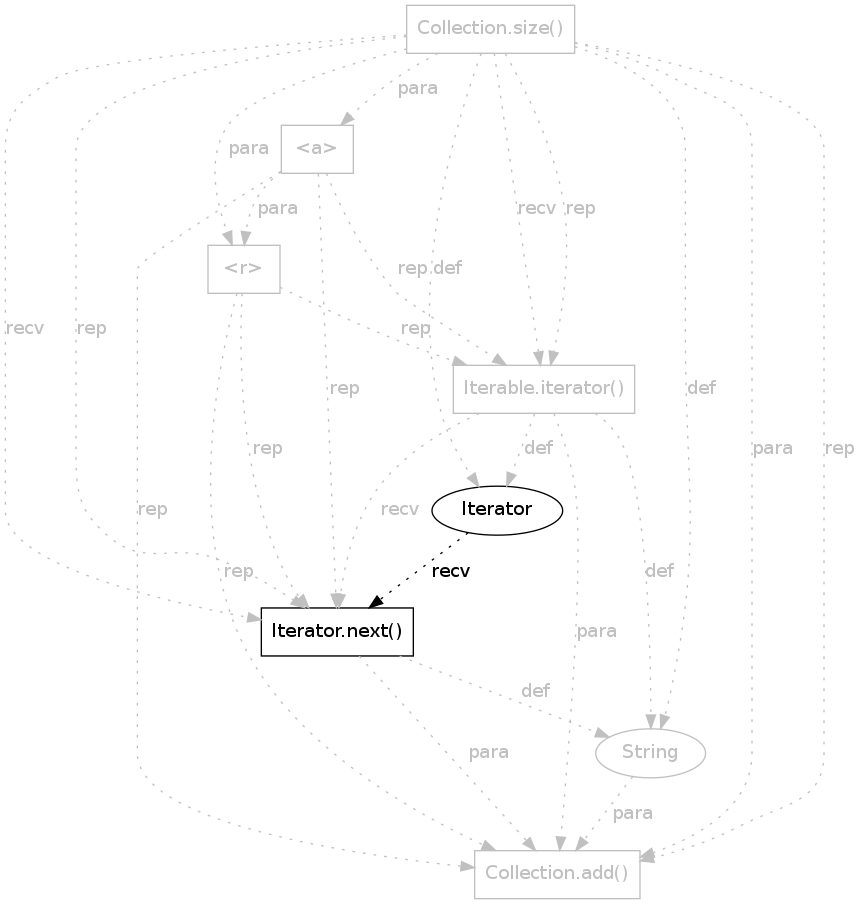
|
|
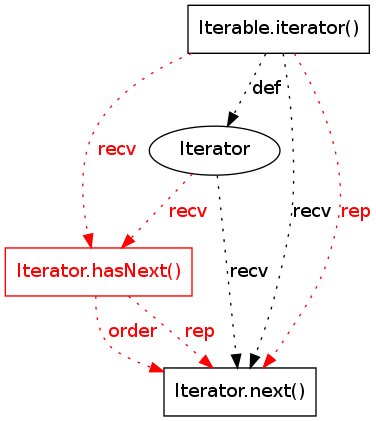
?
|
1609 |
0.24191198 |
((pattern support = 11 / 791)(pattern violations = 1 / 49)(violation support = 1 / 10)(overlap = 1 - (2 / 12))) / 4 |
11 |
|
|
|
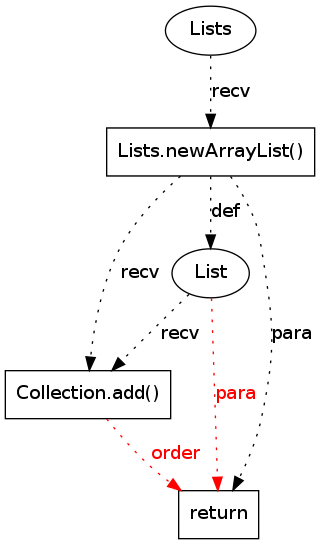
?
|
2159 |
0.2339721 |
((pattern support = 28 / 791)(pattern violations = 1 / 120)(violation support = 1 / 17)(overlap = 1 - (2 / 12))) / 4 |
28 |
|
|
|
?
|
2164 |
0.2339721 |
((pattern support = 28 / 791)(pattern violations = 1 / 120)(violation support = 1 / 17)(overlap = 1 - (2 / 12))) / 4 |
28 |
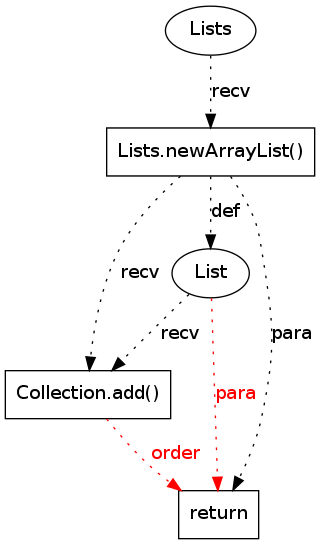
|
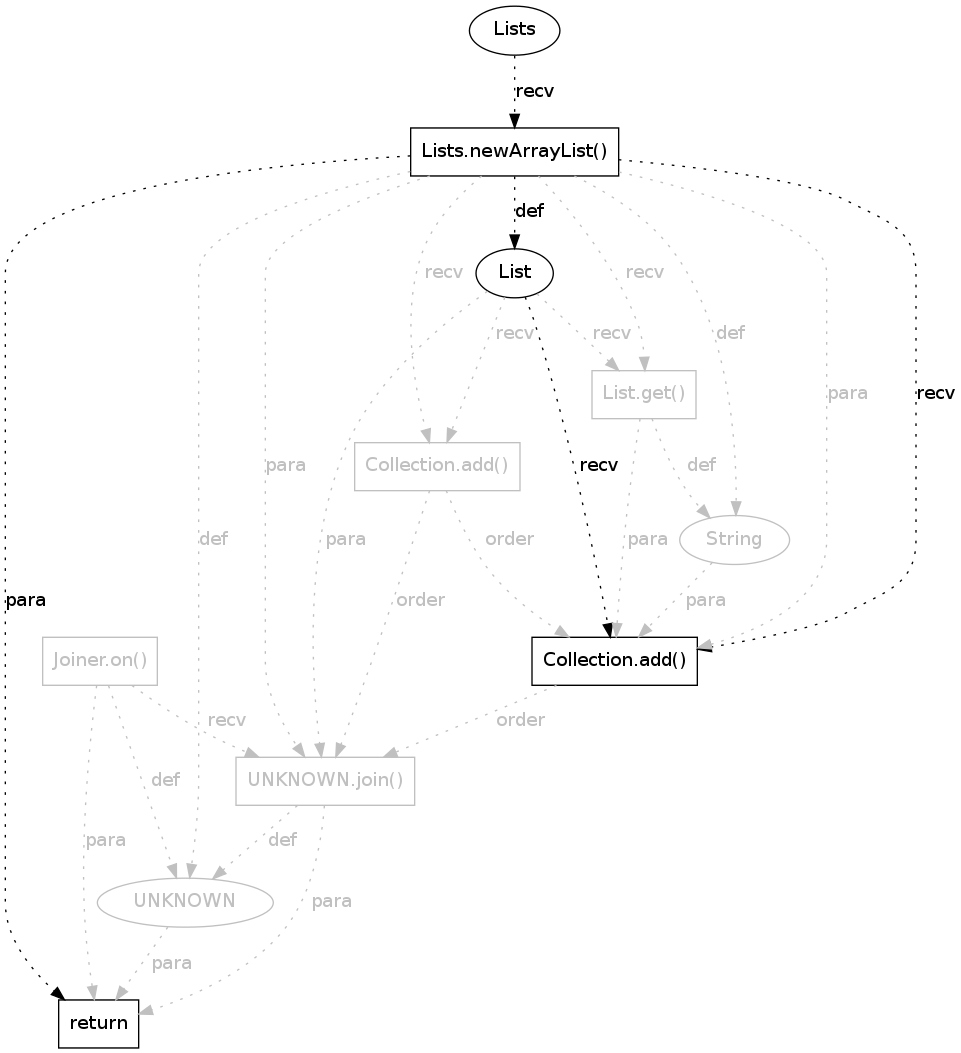
|
|
?
|
2341 |
0.22907186 |
((pattern support = 11 / 791)(pattern violations = 1 / 60)(violation support = 1 / 10)(overlap = 1 - (3 / 14))) / 4 |
11 |
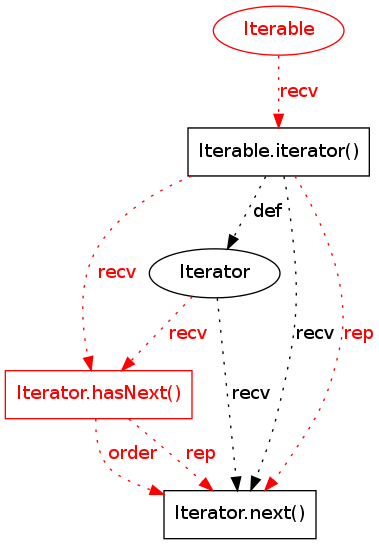
|
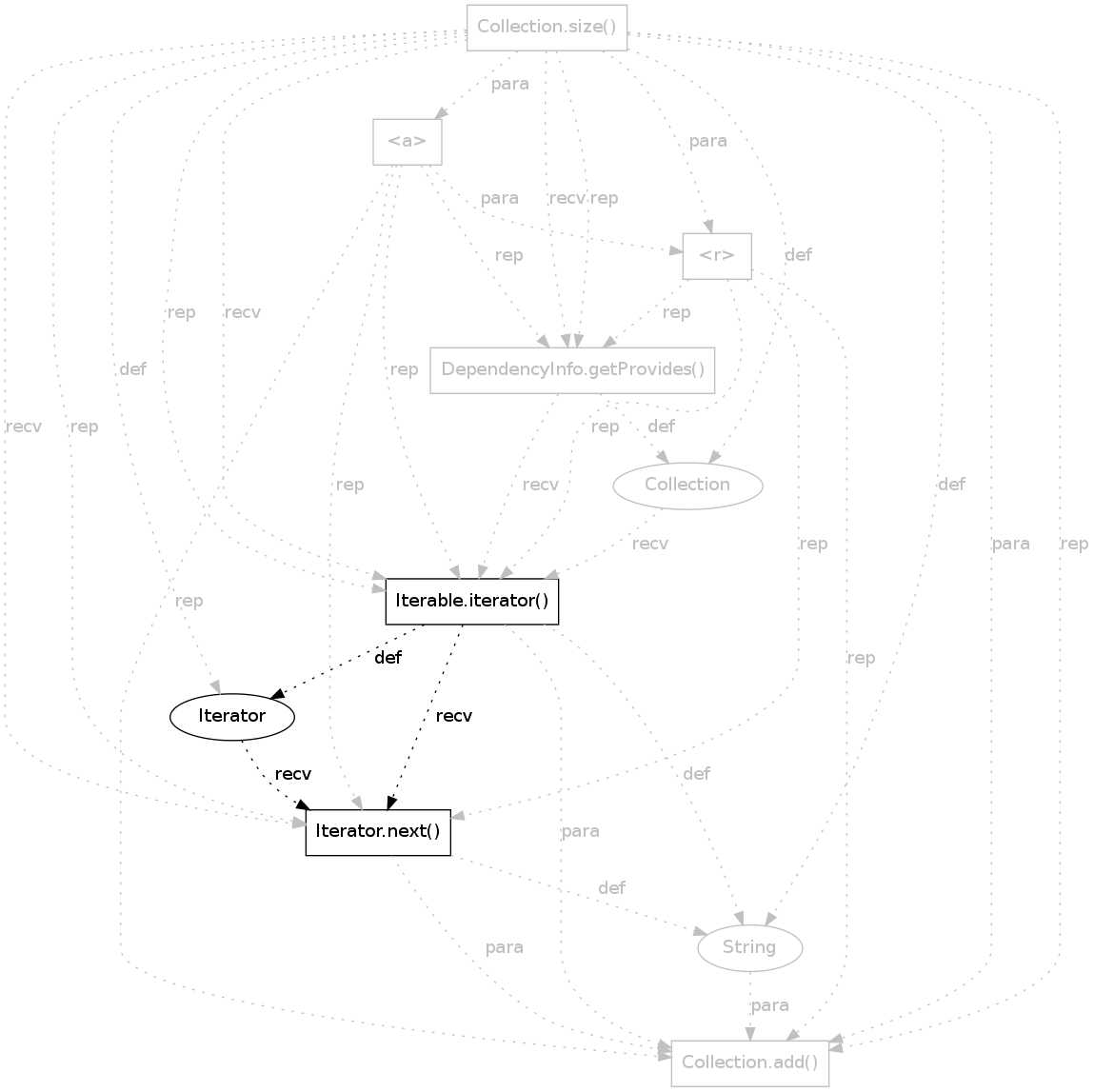
|